Top 10 wifi hacking tools in kali linux
Содержание:
- Course content
- Preparation6 lectures • 20min
- Network Basics4 lectures • 15min
- Gather AP information Before Cracking5 lectures • 17min
- Cracking WEP Encryption8 lectures • 47min
- Cracking WPA/WPA2 Encryptions11 lectures • 58min
- Man in the Middle Attacks16 lectures • 1hr 27min
- Fully accessing the connected devices5 lectures • 27min
- Protect your WiFi AP and yourself against all the previous attacks5 lectures • 29min
- Шаг 1а — Настройка MadWifi -NG
- 6 oclHashcat
- 1 Aircrack-ng
- Known problems that are faced — Troubleshooting
- Шаг 4 — Aircrack-ng — взлом предварительного ключа
- 2 Reaver
- 9 Crunch
- 3 Pixiewps
- Instructor
- Instructor
- 5 Wireshark
- Working Of WPS
Course content
12 sections • 65 lectures • 5h 12m total length
Expand all sections
Preparation6 lectures • 20min
-
Installing Kali Linux 2.0 as ISO file
Preview06:10
-
Installing Kali Linux 2.0 as a Virtual Machine (VirtualBox)
04:52
-
Installing Kali Linux 2.0 as a Virtual Machine (VMware)
Preview02:37
-
Setup Windows as a Virtual Machine
02:52
-
Connecting WiFi Card to the Virtual Machine
Preview01:29 -
Updating Kali LInux 2.0
Preview01:35
Network Basics4 lectures • 15min
-
Network Basics explain
Preview02:36
-
What is the Mac address? and how you can change it?
05:23
-
Enabling monitor mode on the WiFi card
05:29
-
Gather Acess Point information introduction
01:22
Gather AP information Before Cracking5 lectures • 17min
-
Scanning for the available Wi-Fi APs around us
02:42
-
Capturing a specific Wi-Fi access point packets
Preview03:19
-
Disconnecting any device from any access point
03:34
-
Detecting the hidden WiFI Networks (ESSIDs)
Preview02:44
-
Jamming any WiFi access point
04:41
Cracking WEP Encryption8 lectures • 47min
-
introduction
01:31
-
Cracking WEP encryption explain
02:16
-
Cracking WEP encryption methods
Preview01:39
-
Cracking WEP encryption demo
06:44
-
Fake authentication with the target network
04:24
-
Cracking WEP using Korek Chopchop Attack
12:59
-
Cracking WEP using ARP Request Replay Attack
07:15
-
Cracking WEP using Hirte Attack
10:25
Cracking WPA/WPA2 Encryptions11 lectures • 58min
-
Cracking WPA/WPA2 encryptions explain
Preview01:12
-
Cracking WPA/WPA2 encryption methods
01:40
-
Cracking WPA/WPA2 using WPS feature
06:38
-
Capturing the Handshake
04:20
-
Creating a Wordlist
05:55
-
Cracking WPA/WPA2 using dictionary attack
05:17
-
Cracking WPA/WPA2 using bruteforce attack
06:07
-
Cracking WPA/WPA2 using Rainbow Table
05:39
-
Cracking WPA/WPA2 using Hashcat (GPU)
05:25
-
Cracking WPA/WPA2 using Evil Twin attack
11:35
-
Getting the username and the password of the target router
04:32
Man in the Middle Attacks16 lectures • 1hr 27min
-
introduction
Preview01:12
-
Gathering information about the connected clients
02:59
-
Gather detailed information about the clients
07:10
-
Man in the middle attack explain
03:40
-
MITM attack using (arpspoof)
07:24
-
Capturing login credentials
05:23
-
Bypassing SSL Certificate
06:38
-
Redirect any client from to any website
06:32
-
Stealing the Cookies
07:02
-
Capture a screenshot from the target browser
04:12
-
Injecting a keylogger into the target webpage
04:49
-
Capturing images from the network traffic
03:35
-
Injecting html file and flip the images in the target browser
06:48
-
Injecting JavaScript URL and Hooking the client’s with BeEF
06:58
-
Stealing the Target accounts with BeEF
03:45
-
Having Fun with BeEF
08:49
Fully accessing the connected devices5 lectures • 27min
-
Creating an encrypted Backdoor
04:47
-
Testing the Backdoor in the target device
04:29
-
Creating a Fake browser Update & and Hack any client
04:49
-
Interacting with the Target Computer (Part 1)
06:29
-
Interacting with the Target Computer (Part 2)
06:11
Protect your WiFi AP and yourself against all the previous attacks5 lectures • 29min
-
Protect your WiFi access point
07:39
-
Detect ARP Poisoning attack using (XARP)
03:21
-
Detect ARP Poisoning attack (Wireshark)
05:34
-
Prevent your ARP table from poisoning
05:51
-
Detect and Kill any Meterpreter Session
06:14
Шаг 1а — Настройка MadWifi -NG
Сперва остановим ath0, выполнив:
airmon-ng stop ath0
Должно быть так:
Interface Chipset Driver wifi0 Atheros madwifi-ng ath0 Atheros madwifi-ng VAP (parent: wifi0) (VAP destroyed)
Выполните команду «iwconfig», чтобы убедиться в том, что больше никаких интерфейсов athX не запущено. Это должно выглядеть примерно так:
lo no wireless extensions. eth0 no wireless extensions. wifi0 no wireless extensions.
Теперь введите следующую команду, чтобы переключить беспроводную карту на канал 9 в режиме мониторинга:
airmon-ng start wifi0 9
После этой команды мы должны увидеть что-то похожее на:
Interface Chipset Driver wifi0 Atheros madwifi-ng ath0 Atheros madwifi-ng VAP (parent: wifi0) (monitor mode enabled)
Теперь убедимся что наш интерфейс правильно настроен, снова выполняем команду iwconfig
Ответ должен выглядеть так:
lo no wireless extensions.
wifi0 no wireless extensions.
eth0 no wireless extensions.
ath0 IEEE 802.11g ESSID:"" Nickname:""
Mode:Monitor Frequency:2.452 GHz Access Point: 00:0F:B5:88:AC:82
Bit Rate:0 kb/s Tx-Power:18 dBm Sensitivity=0/3
Retry:off RTS thr:off Fragment thr:off
Encryption key:off
Power Management:off
Link Quality=0/94 Signal level=-95 dBm Noise level=-95 dBm
Rx invalid nwid:0 Rx invalid crypt:0 Rx invalid frag:0
Tx excessive retries:0 Invalid misc:0 Missed beacon:0
6 oclHashcat
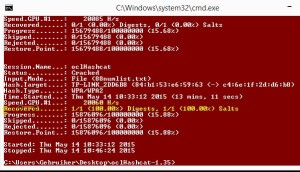
Number 6 in our Top 10 Wifi Hacking Tools is oclHashcat. oclHashcat is not a dedicated Wifi hacking tool and is not included with Kali Linux, but it can do brute force and dictionary attacks on captured handshakes very fast when using a GPU. After using the Aircrack-ng suite, or any other tool, to capture the WPA handshake you can crack it with oclHashcat using your GPU. Using a GPU with oclHashcat, instead of a CPU with Aicrack-ng, will speed up the cracking process a lot. An average GPU can try about 50.000 combinations per second with oclHashcat.
oclHashcat is available for Windows and Linux and has a version for AMD and Nvidia video cards. AMD video cards require Catalyst 14.9 exactly and Nvidia video cards require ForceWare 346.x or later to work.
Website: https://hashcat.net/oclhashcat/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/cracking-wpa-oclhashcat-gpu/
1 Aircrack-ng
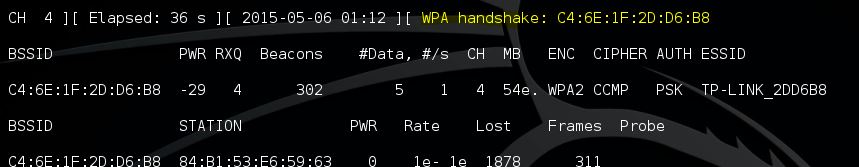
Aircrack is one of the most popular tools for WEP/WPA/WPA2 cracking. The Aircrack-ng suite contains tools to capture packets and handshakes, de-authenticate connected clients and generate traffic and tools to perform brute force and dictionary attacks. Aicrack-ng is an all-in-one suite containing the following tools (among others):
– Aircrack-ng for wireless password cracking
– Aireplay-ng to generate traffic and client de-authentication
– Airodump-ng for packet capturing
– Airbase-ng to configure fake access points
The Aicrack-ng suite is available for Linux and comes standard with Kali Linux. If you plan to use this tool you have to make sure your Wifi card is capable of packet injection.
Website: https://www.aircrack-ng.org/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/how-to-hack-upc-wireless-networks/
Known problems that are faced — Troubleshooting
- As in the pic above, you saw the first line read «Switching wlan0 to channel 6». (Yours will be mon0 instead of wlan0). Sometimes, it keeps switching interfaces forever.
- Sometimes it never gets a beacon frame, and gets stuck in the waiting for beacon frame stage.
- Sometimes it never associates with the target AP.
- Sometimes the response is too slow, or never comes, and a (0x02) or something error is displayed.
In most cases, such errors suggest-
- Something wrong with wireless card.
- AP is very choosy, won’t let you associate.
- The AP does not use WPS.
- You are very far from the AP.
- Rate Limiting implemented in the router (most new router have this)
Possible workarounds-
Шаг 4 — Aircrack-ng — взлом предварительного ключа
На данном этапе нам нужно взломать предварительный ключ WPA/WPA2. Чтобы сделать это, нам понадобиться словарь слов в качестве входных данных.
Существует небольшой словарь, который поставляется с aircrack-ng — “password.lst”. Будем использовать его.
Откройте другой сеанс консоли и введите:
aircrack-ng -w password.lst -b 00:14:6C:7E:40:80 psk*.cap
Где:
-w password.lst это имя файла словаря
*.cap название группы файлов, содержащих перехваченные пакеты
Обратите внимание, что в данном случае мы использовали специальный символ *, чтобы включить несколько файлов.. Вот типичный вывод, когда нет хэндшейков:
Вот типичный вывод, когда нет хэндшейков:
Opening psk-01.cap Opening psk-02.cap Opening psk-03.cap Opening psk-04.cap Read 1827 packets. No valid WPA handshakes found.
Когда это происходит, вы должны либо повторить шаг 3 или ждать дольше, если вы используете пассивный подход.
Вот таким может быть вывод если хэндшейк будет найден:
Opening psk-01.cap Opening psk-02.cap Opening psk-03.cap Opening psk-04.cap Read 1827 packets. # BSSID ESSID Encryption 1 00:14:6C:7E:40:80 teddy WPA (1 handshake) Choosing first network as target.
Теперь в этот момент, Aircrack-ng начнет пытаться взломать предварительный ключ. В зависимости от скорости вашего процессора и размера словаря, это может занять много времени.
Вот таким будет вывод при успешном взломе:
Aircrack-ng 0.8
2 keys tested (37.20 k/s)
KEY FOUND!
Master Key : CD 69 0D 11 8E AC AA C5 C5 EC BB 59 85 7D 49 3E
B8 A6 13 C5 4A 72 82 38 ED C3 7E 2C 59 5E AB FD
Transcient Key : 06 F8 BB F3 B1 55 AE EE 1F 66 AE 51 1F F8 12 98
CE 8A 9D A0 FC ED A6 DE 70 84 BA 90 83 7E CD 40
FF 1D 41 E1 65 17 93 0E 64 32 BF 25 50 D5 4A 5E
2B 20 90 8C EA 32 15 A6 26 62 93 27 66 66 E0 71
EAPOL HMAC : 4E 27 D9 5B 00 91 53 57 88 9C 66 C8 B1 29 D1 CB
Ну вот, ключ у нас. Беспроводная сеть проверена на безопасность 😉
2 Reaver
Number 2 in the Top 10 Wifi Hacking Tools is Reaver. Reaver is another popular tool for hacking wireless networks and targets specifically WPS vulnerabilities. Reaver performs brute force attacks against Wifi Protected Setup (WPS) registrar PINs to recover the WPA/WPA2 passphrase. Since many router manufacturers and ISPs turn on WPS by default a lot of routers are vulnerable to this attack out of the box.
In order to use Reaver you need a good signal strength to the wireless router together with the right configuration. On average Reaver can recover the passphrase from vulnerable routers in 4-10 hours, depending on the access point, signal strength and the PIN itself off course. Statistically you have a 50% chance of cracking the WPS PIN in half of the time.
Website: https://code.google.com/p/reaver-wps/
Tutorial: https://www.hackingtutorials.org/wifi-hacking/pixie-dust-attack-wps-in-kali-linux-with-reaver/
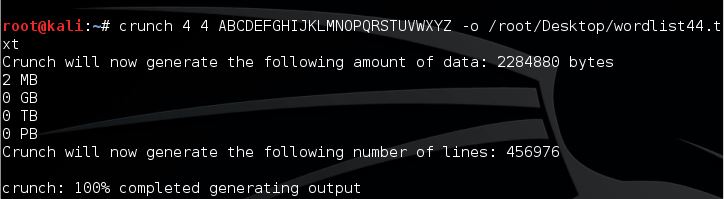
9 Crunch
Crunch is a great and easy to use tool for generating custom wordlists which can be used for dictionary attacks. Since the success rate of every dictionary attack depends on the quality of the used wordlist, you cannot avoid creating your own wordlist. Especially when you want to create wordlists based on default router passwords. Crunch can also be piped directly to other tools like Aircrack-ng. This feature can save a lot of time since you won’t have to wait until large password lists have been generated by Crunch before you can use them.
Website: https://sourceforge.net/projects/crunch-wordlist
Tutorial: https://www.hackingtutorials.org/general-tutorials/password-list-with-crunch/
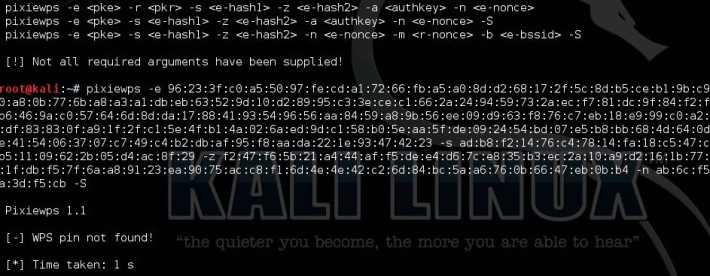
3 Pixiewps
PixieWPS is a relatively new tool included with Kali Linux and also targets a WPS vulnerability. PixieWPS is written in C and is used to brute force the WPS PIN offline exploiting the low or non-existing entropy of vulnerable access points. This is called a pixie dust attack. PixieWPS requires a modified version of Reaver or Wifite to work with. Since this tools has become quite popular in little time, it earns the number 3 in our Top 10 Wifi Hacking Tools list.
Website: https://github.com/wiire/pixiewps/
Modified Reaver: https://github.com/t6x/reaver-wps-fork-t6x
Tutorial: https://www.hackingtutorials.org/wifi-hacking/pixie-dust-attack-wps-in-kali-linux-with-reaver/
Instructor
Saad Sarraj
Ethical Hacker, IT Expert
- 4.5 Instructor Rating
- 1,228 Reviews
- 11,444 Students
- 4 Courses
My Name is Saad Sarraj, I am an Ethical Hacker who is trying to keep the internet more secure. I have a very good Experience in Penetration Testing. I started in this field since 2012, then I have created my own website that covers some topics in IT in general and Cybersecurity in particular then I made a YouTube channel that includes many tips and tricks in using Linux OS and Windows OS. I always focus on the practical side without neglecting the theory behind every single (attack, technique, idea). I am sharing my experience with you from what I previously learned.
Show moreShow less
Instructor
Rene T
Incident Responder and SecOps Specialist
- 4.2 Instructor Rating
- 21 Reviews
- 179 Students
- 1 Course
International (Hands-on) Independent Emergency Incident Responder, Investigator, Threat Hunter, Pen Tester and Instructor. I have also been a CISO and have cybersecurity management experience, and have implemented security programs and built SECOPS teams for multinational corporations and governments.I am an accomplished and technical strong information security professional with 22+ years within IT and cybersecurity, establishing, running and leading Security Operations, SOC and IR teams. I come from a technical and hands-on background (yet strong academic aptitude). I also operate well in the strategic and GRC side of IT security, and have even mentored students in cutting-edge cybersecurity research projects as a university lector. I hold a MSc in Digital Forensics and Cybersecurity (with distinction) and was module leader and created several online modules for the national MBA in cybersecurity. I have taught Digital Forensics, Ethical Hacking and Incident Response at master and bachelor level as well as industry 3-10 days full courses in Analysing Malware, Incident Response, Security Operations and Threat Hunting.
I hold several industry certifications and believe in continuous development – Never stop learning! Some of the certifications I hold (or held) are:
GCIH (SANS Certified Incident Handler)
eCTHP (Certified Threat Hunter Professional)
OSWP (Offensive Security Wireless Professional)
CISM (Certified Information Security Manager)
CISSP (Certified Information Systems Security Professional)
CSPT (Certified Security Testing Professional – Web Apps)
CIPR (GCHQ-Certified Cyber Incident Planning & Response)
CEH (Certified Ethical Hacker) Certified by EC-Council
Acunetix Certified
ACE (AccessData Certified Examiner, Digital Forensics)
CHFI (Certified Hacking Forensic Investigator)
CEPT (Certified Expert Penetration Tester – IACRB)
CREA (Certified Reverse Engineering Analyst — IACRB)
CCFE (Certified Computer Forensics Examiner — IACRB)
ISO 27001 Lead Implementer – IBITGQ
GDPR DPO PractitionerWhen teaching, presenting or mentoring, I often get the feedback «your passion for your chosen subject is infectious!». I want to make a difference and believe in the statement “Choose a job you love, and you will never have to work a day in your life».
Show moreShow less
5 Wireshark
Wireshark is one of the best network protocal analyzer tools available, if not the best. With Wireshark you can analyse a network to the greatest detail to see what’s happening. Wireshark can be used for live packet capturing, deep inspection of hundreds of protocols, browse and filter packets and is multiplatform.
Wireshark is included with Kali Linux but also available for Windows and Mac. For certain features you do need a Wifi adapter which is supports promiscuous and monitoring mode.
Website: https://www.wireshark.org
Tutorial: https://www.howtogeek.com/104278/how-to-use-wireshark-to-capture-filter-and-inspect-packets/
Or follow one of these online courses:
– Wireshark Crash Course
– Wireshark Tutorial – Get Wireshark Certification
Working Of WPS
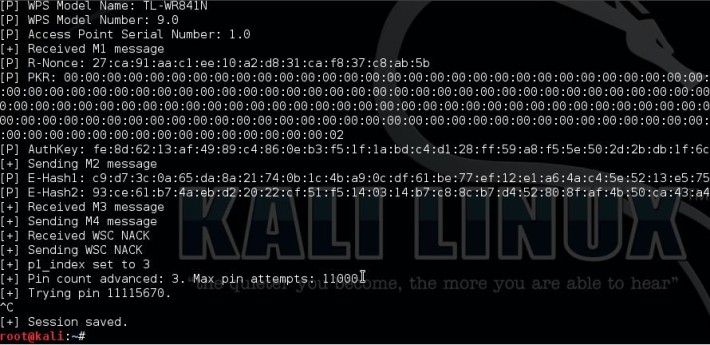
Now while most of the things are the same as in WPA, there is a new concept of using pins for authentication. So basically, the client sends 8 digit pins to the access point, which verifies it and then allows the client to connect. Now a pin has 8 digits, and only contains numbers, so its a possible target for bruteforece. Under normal bruteforcing of WPA passwords, you have to consider the fact that there may be number, alphabets, and sometimes symbols (and more than 8 letters). This make the task a billion billion times tougher. However, we can try thousands of keys per second, which make it a tad bit easier. Now in WPS, there is a delay because we have to wait for APs response, and we may only try a few keys per second (practically the best I’ve seen on my PC is 1 key per 2 sec). Basically, 8 digits and 10 possibilities per digit (0-9) make it 10^8 (interpret ^ as raised to the power of)seconds if we assume one key per second. Now that’ll be years. So, where is this taking us? The answer is, there are flaws in this technology that can be used against it.
- The 8th digit is a checksum of first 7 digits. 10^7 possibilities, i.e. one-tenth time. Two months, still a way to go.
- The pin number for verification goes in two halves, so we can independently verify the first four and the last four digits. And believe me, its easy to guess 4 digits correct two times, than to guess 8 correct digits at once. Basically, the first half would take 10^4 guess and the second would take 10^3.
Now the guesses would be 10^4 + 10^3 (not 10^4 *10 ^3). Now we need 11,000 guesses.
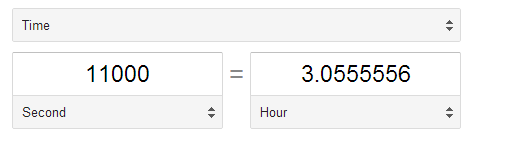
So that’ll take 3 hours approximately. And that’s all the combinations, and most probably the correct pin will not be the last combination, so you can expect to reach the result earlier. However, the assumption is that bruteforcing will take place at a key per second. My personal best is a key every 2 seconds, and yours might drop to as low as a key every 10 seconds.
How to carry out the attack
Now it might have been tough to carry out this attack at some point in history, but now, its a breeze. If you have all the prerequisites, then hacking the network would be as easy as